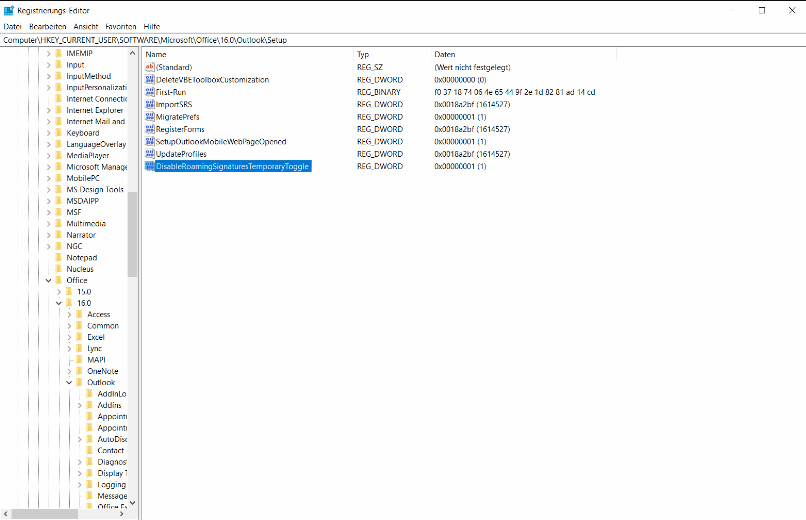
You might have heard about CVE-2023-23397 a vulnerability targeting Microsoft Outlook. The exploit can be triggered without user interaction. The vulnerability seems easy to exploit. Fortunately, you can simply protect yourself: Update Outlook/Office Apps and you are good.
But how can we make sure we have not been exploited by that vulnerability? Microsoft has released a script for local Exchange installations as well for Exchange Online/ Microsoft 365.
This blog post shows how to use the Script to identify potential malicious mails in M365.
First we need to start Powershell as administrator. After that we install the AzureAD module:
PS C:\Users\Administrator> Install-Module AzureAD
Powershell will then ask if the module should be installed from an external source. Please select Yes (Y) here.
Next, we need to install the Exchange Online module:
PS C:\Users\Administrator> Install-Module -Name ExchangeOnlineManagement -RequiredVersion 3.1.0
Powershell will then ask again if the module should be installed from an external source. Please select Yes (Y) again.
The script used in the following step can be downloaded from here.
Now we need to create an AzureAD application, which is needed to check the mailboxes:
PS C:\Users\Administrator\Downloads> .\CVE-2023-23397.ps1 -CreateAzureApplication
Depending on the Powershell configuration, it may be necessary to confirm again that the script may be executed. You can either chose (M) or (A). I recommend chosing M.
A new window will open to log in to M365 as a global administrator or application administrator.
If your output is similar to the following creating the helper application has worked:
CVE-2023-23397 script version 23.03.15.2119
Prompting user for authentication, please minimize this window if you do not see an authorization prompt as it may be in the background
Adding user adminuser@yourtenant.com as owner of CVE-2023-23397Application
Setting Azure AD Permissions
Assigning Necessary Azure AD Service Roles
Application created with required permissions. Client ID: xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx
After this step we now can start the investigation. We need to connect to Exchange Online first:
PS C:\Users\Administrator\Downloads> Connect-ExchangeOnline
You might need to re-authenticate at this point to M365. (I did not need to log in again at this step)
And then we can start the Powershell script to search for malicious files (If you selected (M) when running the script for the first time, you must confirm execution again now):
PS C:\Users\Administrator\Downloads> Get-Mailbox -ResultSize Unlimited | .\CVE-2023-23397.ps1 -Environment "Online"
At this point it is mandatory to authenticate again. Output should be similar to the following:
CVE-2023-23397 script version 23.03.15.2119
Trying to find Microsoft.Exchange.WebServices.dll in the script folder
Microsoft.Exchange.WebServices.dll wasn't found - attempting to download it from the internet
Prompting user for authentication, please minimize this window if you do not see an authorization prompt as it may be in the background
Waiting 60 seconds for app credentials to register..
Continuing...
Scanning 1 of 16 mailboxes (currently: mailbox1@yourtenant.com)
Scanning 2 of 16 mailboxes (currently: mailbox2@yourtenant.com)
Scanning 3 of 16 mailboxes (currently: mailbox3@yourtenant.com)
Scanning 4 of 16 mailboxes (currently: mailbox4@yourtenant.com)
Scanning 5 of 16 mailboxes (currently: mailbox5@yourtenant.com)
[...]
Scanning 16 of 16 mailboxes (currently: mailbox16@yourtenant.com)
No vulnerable item found
Do you have feedback regarding the script? Please email ExToolsFeedback@microsoft.com.
I hope you will see the same output as I do. The script also supports deleting affected files. For more information please look at Microsofts script documentation.
After checking the mailboxes, we no longer need the AzureAD Helper Application. To delete the application just run the following command:
PS C:\Users\Administrator\Downloads> .\CVE-2023-23397.ps1 -DeleteAzureApplication
You have probably already guessed: First you have to allow the script again and thereafter you have to authenticate to Microsoft 365 a last time 😉
I hope the explanation helped you to check your tenants. Feel free to let me know if it worked or if you had any problems with it.